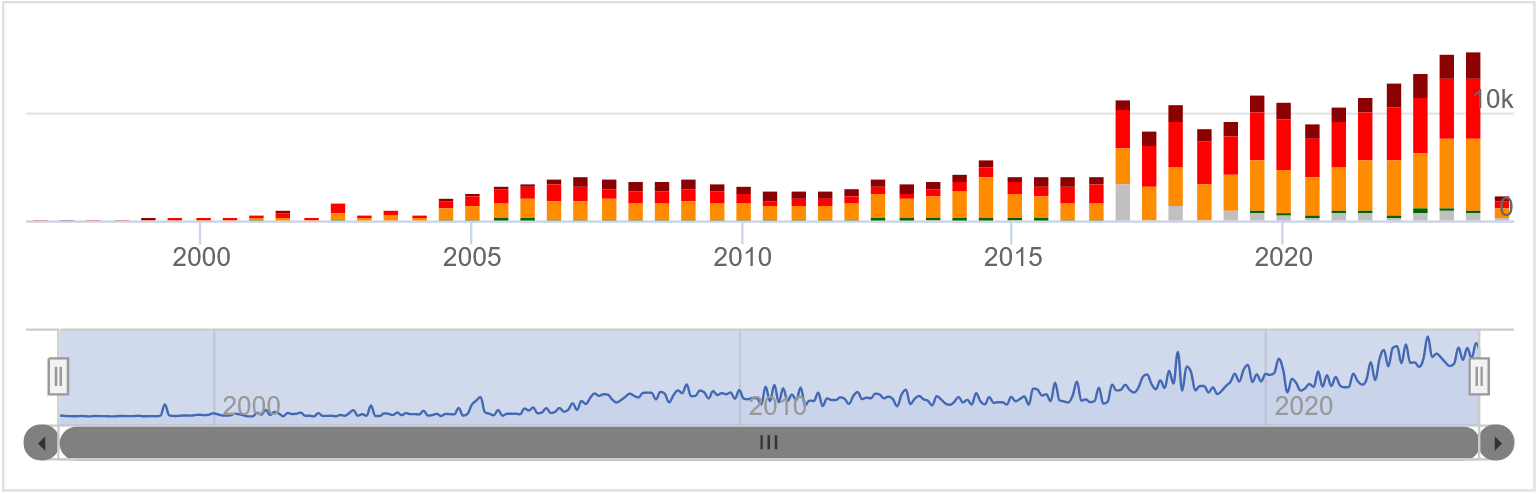
Checking your systems for vulnerabilities daily is essential. Worldwide, over 60% of all successful cyber-attacks occur directly through vulnerabilities for which solutions were available at the time of the attack.
Over 60% of all cyber-attacks could have been prevented by using free patches and updates. Yet, even years-old vulnerabilities are often exploited because they were overlooked. These open vulnerabilities provide attackers with easy and cost-effective access to companies.
Our scanning service alerts you immediately to critical vulnerabilities, allowing you to close them in time.